How to Find the Md5 Sum of the Uploaded File Using Wireshark
byBenjamin S. Williams
Full content parcel captures can provide valuable insight into an assay or investigation. Depending on the placement of the capture device, an analyst is sometimes able to recreate an exact timeline of events between two or more hosts. A key component of this process is beingness able to replicate content transferred between hosts based solely on the packet capture. With a full content packet capture it is possible to extract a fleck-for-chip copy of files transferred between hosts across many awarding-layer protocols, both TCP and UDP based.
This will demonstrate a simple method of extracting an executable transferred across an FTP session identified in a packet capture. The but tool required is Wireshark which is freely bachelor for Mac, Linux, and Windows operating systems. In that location are tools available which automate this process in many scenarios, only forensic analysts should understand the underlying concepts so, in the case that an automated tool falls short, files can exist extracted manually.
In testing, a lab environment was setup with ii hosts – a Linux FTP server 192.168.1.68 and a Mac client 192.168.ane.2. A win32 executable original.exe is located on the FTP server, which volition be downloaded to my Mac client as copy.exe. Quite often the forensic analyst volition not accept access to either the client or server systems, merely for the sake of demonstration the md5-hash of original.exe file on the server is shown:
bwilli@bwilli-desktop:~/Documents/weblog$ ls -l
total 1496
-rw-r--r-- 1 bwilli bwilli 1531593 2011-01-26 17:43 original.exe
bwilli@bwilli-desktop:~/Documents/weblog$ md5sum original.exe
4c0f858d4183d733510dc7dbb6fe63dd original.exe
With the bundle capture running, login to the FTP server from the Mac client and transfer the file original.exe (saving it to the Mac client as copy.exe). At this point, assay of the packet capture begins (Figure one).
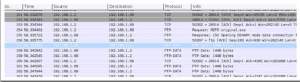
Figure 1 – Packet Capture showing FTP traff
After reviewing the FTP login, directory listings, and other user commands, I've identified the FTP RETR command issued by the customer in packet #154. This is where the Mac client actually requests a file from the FTP server. With this being an FTP session, the filename is shown and the file requested appears to be an executable (original.exe). This helps remove some of the judge-work in verifying the file signature later. Packet #157 is where the actual file transfer begins, which is viewable in Wireshark as its own TCP stream. Merely correct-click packet #157 and select "Follow TCP Stream" to view the data transfer session of original.exe between 192.168.1.68 and 192.168.1.2.
This brings upwards a Stream Content window within Wireshark which shows, in raw bytes, the information transferred betwixt the FTP server and the Mac client. Since the server has been identified equally 192.168.i.68, this is the host responsible for sending the raw contents of original.exe beyond the network. Within the Stream Content window of Wireshark, Change the display from "Entire Conversation" to show only the data sent from the FTP server (Figure 2):

Figure ii – Selecting Only Data Sent from Server to Client
For FTP traffic the above footstep doesn't make a difference in one case a "Follow TCP Stream" is performed, but for some protocols this volition be necessary.
Next, switch the Stream Content view from 'Raw' to 'Hex Dump' to verify the file signature. This option is located in the lower right-manus corner of the "Follow TCP Stream" window. Win32 executables take a file signature of 0x4d 0x5a. The beginning two bytes seen within this transfer are a match (Effigy 3), which shows this is a true executable.

Effigy 3 – Hex Dump View of the File Transfer
At this indicate, switch dorsum to 'Raw' view and click "Save As" to consign the raw data to a file. I saved the file asftpfile without an extension. This is washed to double bank check the final result with the file control before assigning a filename:
-rw-r--r-- one bwilliams staff 1531593 Jan 26 21:thirteen ftpfile
my-macbook-pro:blog bwilliams$ file ftpfile
ftpfile: PE32+ executable for MS Windows (GUI) Mono/.Net assembly, RAR cocky-extracting annal
The md5 hash of the extracted file exactly matches that of the original file observed on the server:
my-macbook-pro:weblog bwilliams$ md5 ftpfile
MD5 (ftpfile) = 4c0f858d4183d733510dc7dbb6fe63dd
This is a fundamental method of reconstructing data identified within a full content parcel capture. This could help in tracking user actions, identifying malware, and enumerating data exfiltration among numerous other uses.
arcandshouthat1978.blogspot.com
Source: https://crucialsecurity.wordpress.com/2011/02/24/extracting-files-from-packet-captures/
Post a Comment for "How to Find the Md5 Sum of the Uploaded File Using Wireshark"